Protecting Against "Trojans"
Contents
- 1 Team Information
- 2 Technology & Issue
- 3 Initial Project Statement
- 4 Introduction to Trojans
- 5 How a Trojan Horse Virus is Distributed
- 6 What is Anti-Virus Software?
- 7 How well does anti –virus protection protect, disinfect, and quarantine Trojans from your computer
- 8 Is Anti-Virus Necessary?
- 9 Conclusion
- 10 References (online Sources)
- 10.1 What is a Trojan Virus?(Kathryn Dupuis)
- 10.2 What applications (sites/ emails/ downloads) infect your computer with Trojans (Santi Churphongphun)
- 10.3 What is anti – virus protection? (Mark Sauverwald)
- 10.4 (Effectiveness) How well does anti –virus protection protect, disinfect, and quarantine Trojans from your computer. (Brad Soon)
Team Information
Group Name:
The Trojan warriers
Group Members:
Kathryn (Katie) Dupuis
Brad Soon
Santi Churphongphun
Mark Sauverwald
Group Member Contact Information:
Kathryn (Katie) Dupuis - kldupuis@ucalgary.ca
Brad Soon - btsoon@ucalgary.ca
Santi Churphongphun -sgchurph@ucalgary.ca
Mark Sauverwald - namadoor@gmail.com
Technology & Issue
Technology: Trojan Viruses
Issue: How to protect your computer from Trojan Viruses
Initial Project Statement
The technology that our group has chosen to look at is Trojan Viruses, and the issue that we will be focusing on is how you can protect your computer from Trojan viruses. We will investigate what a Trojan virus is, how it affects your computer once infected, and look at examples of existing Trojans. In addition, we will look at the threat of your computer being infected with a Trojan when you are on the internet showing which types of sites and applications that you are most likely to receive a Trojan from. We will then look at the different types of Anti-virus software and argue whether the average user should have Anti-virus protection based on how effectively they protect, disinfect, and quarantine most Trojans.
Introduction to Trojans
A Trojan is a piece of software that appears to be something safe, constructive, or helpful appearing to come from a legitimate source that you download such as a game, picture, music or movie file. However, hidden inside is usually a worm or virus that will cause harm to your computer. They are notorious for being used to install backdoor programs. These backdoors once installed allow malicious users to access your system. They may also cause confidential information to be compromised.
The name comes from the classical myth of the “Trojan Horse” spoken of in Homer’s Iliad. The legend tells of the Greeks using a huge, hollow wooden horse to sneak troops into the fortified city of Troy which allowed their victory in the Trojan war.
Trojans can unleash dangerous programs that can erase your disk, send credit card numbers and passwords to a stranger. A common example of a Trojan is a fake login program, which collects your account information and passwords.
Unlike other viruses Trojans are non- replicating and do not reproduce by infecting files. They do not usually spread by themselves and must be spread by other mechanisms.
“An example of a trojan horse virus would be a virus which required a user to open an e-mail attachment in Microsoft Outlook to activate. Once activated, the trojan horse virus would send copies of itself to people in the Microsoft Outlook address book.” Quoted from http://www.tech-faq.com/trojan-horse-virus.shtml.
For a list of Trojans see: http://www.2-spyware.com/trojans-removal
Here is an example of thee different Trojans and their effect on users systems. From http://www.2-spyware.com/trojans-removal
The Viruscan Trojan is usually run by inexperienced users who believe that it is an antivirus program. While it is being run on their computer the parasite within starts damaging critical parts of the system instead of searching for viruses like the users believe.
Another Trojan is the Pandora Trojan whose name is also taken from Greek mythology. The Pandora Trojan contains a very dangerous and destructive parasite. It works its way into your computer system from insecure internet resources or file sharing networks or programs passed through online chat. It waits until a pre determined date to run its payload which attempts to destroy your entire computer system. It does this by deleting critical system folders like windows or program files or else by formatting the main hard dist.
The AceBot Trojan is a backdoor Trojan designed to perform different destructive actions. Running antivirus programs installed on the targeted computer are detected and disabled. Acebot enables the hacker to remotely control the compromised system by connecting to the Internet Relay Chat (IRC) network. AceBot can also download other harmful parasites from various malicious servers.
How a Trojan Horse Virus is Distributed
Trojan Horse viruses are concealed in programs which look as though they are useful. By visiting a site on the web and downloading a seemingly useful utility program then run it. Once Trojan horses have been produced into ready viruses, they work by fooling an unsuspecting user into executing it. Immediately, your computer system is infected without you even realizing. They can also be transmitted via email attachments. If an email has an attachment which contains an executable file, that file can also contain a Trojan virus which will infect your computer if the program is run. Executable files have extensions such as .exe but on occasion the extensions are altered or hidden altogether to make the file look like a harmless such as a text file so that you open it without hesitation. An illustration of this would be a file named 'over_here.txt.exe. The user may not notice the '.exe' part of the filename (the extension) and believe it to be just a text file. Some operating systems allow users to hide extensions, so in this case the user would only see 'look_at_me.txt'. Newer tactics involve embedding trojans inside image files. Newer tactics involve embedding them in certain image files. The lesson is: never open a file from someone unknown, or when its arrival is unexpected. Even well-meaning individuals pass on viruses this way. There are many negative effects that can result from a Trojan horse virus infecting your PC. For instance if important data is being targeted by the virus they can most likely destroy it completely or render it. The golden rule is to never open a file from an unknown source, or when its arrival is unexpected. Even well meaning individuals pass on viruses this way without even realizing it.
At the same time, it is common for Trojans to be spread through operating system vulnerabilities. An operating system, such as Windows or Linux, controls the basic operating functions of the computer. Computers connect to the Internet through 'ports', some of which present security risks and Malware (malicious software) takes advantage of these vulnerabilities. One of the more well known Trojans is called Sub7. Some claim it has genuine uses, such as remotely controlling your own computer, though it is often used for more malicious activities. Computers with Sub7 installed are accessible from a remote location and can be used to steal credit card numbers or passwords by logging keystrokes for instance.
After the virus has been executed and has begun infecting your PC, the actual results that will come from this can vary. Some Trojan horse viruses will simply be annoying and will not necessarily harm your computer in any way, while others can and will be able to cause serious damage to your computer by deleting files and destroying vital information on your system. There is also the issue of a blended threat, which refers to the matter of a particularly sophisticated attachment which combines some of the worst aspects of viruses, worms. Trojan horse viruses and malicious, which is obviously the most devastating thing. Rather than simply having one type of virus that has been executed they prefer to attack your system. These blended threats are also considered to be the worst case because of the fact that they are the highest risk to security. Make sure that you keep your virus software up to date so that you have good protection. There are some antivirus programs that make you manually scan over your attachments as well as other files that are incoming. You'll want one that does this automatically since the cost difference is slight.
Symptoms of a Trojan virus infection
If you experience any of the following symptoms, you have been infected:
- Your CD-ROM drawer opens and closes by itself. Many Trojans have the ability to open and close your CD-ROM drawer. Two of the most popular Trojans that allow this command are the Netbus and Sub7 Trojans.
- Your mouse moves by itself. The intruder can take control of your pointer and click on icons and start programs as if he/she were sitting in your chair in front of your computer.
- Your screen saver settings change by themselves Often.
What is Anti-Virus Software?
Anti-virus software is a set of tools that are used to minimize your risk of being infected with a computer virus, a worm, a Trojan, spyware or other malicious software commonly referred to as malware. Anti-virus software contains a virus scanner which is used to recognize suspicious coding in computer files. Some anti-virus software packages can also identify abnormal computer activity to block trojans and other viruses. Tools to fix a file infected with a virus or quarantine that file are also included in anti-virus software packages.
The main method anti-virus software uses to keep you computer safe is a virus definition dictionary. This dictionary contains pieces of code from viruses. It will scan the computer’s files to see if it can find a match in the files with one of the pieces of code from the dictionary. If so, the virus scanner will flag the file as infected. The scanning process can be done two ways: on-demand and real time.
On-demand Scanning
On-demand scanning refers to when a virus scanner is instructed to scan the computer’s files for viruses, either by the user or by a scheduled computer event. Once the entire scan is completed, the anti-virus software displays a report for the user, and if any virus was found, asks what move the user wants to take in removing the problem. Original virus scanners used this method almost exclusively, and the on-demand virus scanning engine became the starting point of most internet security software packages for personal computers. There are also many free web-based virus scanning programs available on the internet that rely on this method.
The advantage of on-demand scanning is that the anti-virus program is only using computer resources when the scanner is running, so in between scans your computer is not bogged down by a virus engine. For a computer that has a limited number of files on its hard drive, the scan can be quick. On-demand scanning is also useful is the user believes that he or she may have download a virus either from a website or from an e-mail attachment.
The disadvantage of on-demand scanning is that viruses will not be detected in between scans. If you don’t set your computer to automatically run regular virus scans, you will be responsible for starting any scan you want run on your computer. Many users will forget to scan their computer on a regular basis, allowing for a Trojan or other virus to go undetected on a computer for many weeks. On-demand scanners also have no way of stopping a user from downloading a potential virus. They also do not halt a virus from functioning once it has infected a computer.
Real Time Scanning
Real Time scanning is a much more sophisticated method. In addition to being able to run on-demand scans, real time scanners run a quick virus scan on every file that the user accesses. These scans occur before the file is executed or opened. If a virus is found on the file, the anti-virus software will jump into action and stop the file from being opened or executed. The user will then be informed that a virus was found in the file they were attempting to open. Real time scanners are a lot more effective at finding and stopping viruses and are especially good for people who do not have a whole lot of computer experience. When configured properly, they can stop inexperienced users from opening or downloading dangerous files. If a user believes that his or her computer contracted a virus, he or she is still able to run a full system scan with a built in on-demand scanner.
The main disadvantage of them, however, is the fact that the real time scanner always needs to be running. Since it scans every file before that file before it is allowed to open, they use up system resources effectively slowing down a person’s computer. Real time scanners also need to be loaded when the computer starts up; increasing the amount of time a computer needs to boot.
Most real time scanners fall short of scanning a file before it is opened as well. Instead, the scanner scans the file as it is opened. The user will know if the file was dangerous, however it may be too late to protect his or her computer from the threat. Real time scanners tend to be more expense, and there are few free real time scanners.
Internet Security Suites
Another product available from most computer security companies today is an internet security suite. In addition to providing anti-virus scanning abilities, these suites include tools for keeping your computer free of spyware, adware, and usually also include a firewall. They also include anti-spam programs that help stop junk e-mail messages with popular e-mail programs such as Microsoft Office Outlook.
A useful function of these sophisticated security suites is the ability to prevent Trojans and other viruses is monitoring the computer’s activity for suspicious behaviour. A “zero day” virus is a new virus that has not yet been added to a virus scanner’s definition dictionary. As a result, the computer is open to the new threat. By monitoring the computer for suspicious activity, the anti-virus software may be able to detect a when a file or program is acting in a way that viruses usually act. New virus that is not yet in the scanner’s dictionary can be caught before they do damage to a computer this way.
Monitoring the computer’s activity, however, slows down the computer even more than a regular virus scanner. This security suite is also more expense then either type of virus scanner, and usually contains many tools that beginning users do not know how to use. Configuring a internet security suite can also be tricky for new computer users, and the default “easy setup” options often do not provide the optimum level of security that the security suite is capable of.
Anti-Virus Updates
Both on-demand and real time scanners require that the definition dictionary be up to date for the scanner to function properly. Many new viruses (and Trojans) are created each day, and without a current dictionary of viruses, virus scanning software will not be able to recognize the threat. Almost all anti-virus companies sell subscriptions that allow new virus definitions to be downloaded when they are released by the company. These companies usually charge between $20 and $50 for a one year subscription. If you wish to purchase an internet security suite, you will often end up paying from $50 to $75 per year for a subscription.
Does Anti-Virus Software Stop Trojans?
Anti-virus is only one method for stopping Trojans from getting onto a user’s computer. Unfortunately, like many methods, it does not always work. SubSeven has been a problematic Trojan in the past. It allows for a person employing the SubSeven Trojan to access the system of any computer infected with it. Once the computer is accessed, the malicious user can do whatever he pleases with the computer system, whether it would be harmless or not. SubSeven constantly has new versions being release so that the virus signature does not match the definition in anti-virus software’s definition dictionary.
BioNet is another similar Trojan. Before 2001, it did not pose that great of threat as anti-virus programs could easily detected and stop it. However, a new version released in 2001 took advantage of a way the Windows operating system worked. It was able to disable anti-virus software before the anti-virus software was even able to detect it. It also had a built in feature to corrupt anti-virus software so that the user had to uninstall and reinstall it.
These two examples show that while anti-virus software may help detect and stop Trojans, they are not always effective in battling them, even with constant updates.
The Price of Security
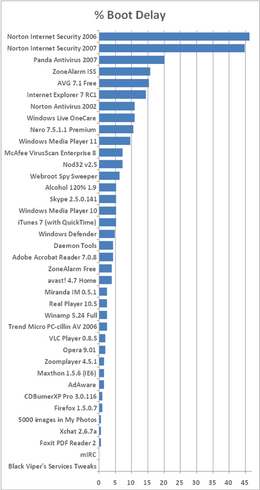
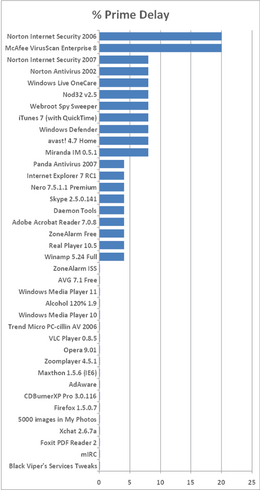
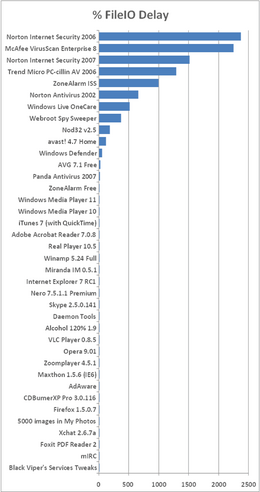
Anti-virus software has an impact on your computer’s performance. Anti-virus software needs to be started when the computer is booted. This will slow down boot times for the computer. Since most anti-virus software these days also runs in the background and scans files before they are opened (real time scanning) the CPU is slowed as well as the hard drive. Sometimes anti-virus scanners can significantly impact and decrease the computer’s overall performance. The following table shows how much performance you are giving up for anti-virus protection.
| Security Suite | Boot % Slower | CPU % Slower | Hard Drive % Slower |
|---|---|---|---|
| Norton Internet Security 2006 | 46% | 20% | 2369% |
| McAfee VirusScan Enterprise 8 | 7% | 20% | 2246% |
| Trend Micro PC-cillin AV 2006 | 2% | 0% | 1288% |
| ZoneAlarm ISS | 16% | 0% | 992% |
| Windows Live OneCare | 11% | 8% | 512% |
| avast! 4.7 Home | 4% | 8% | 115% |
| Panda Antivirus 2007 | 20% | 4% | 15% |
As you can see, hard drive performance is affected the most, but the other main areas of computer performance are affected as well. Performance charts with more anti-virus suites, as well as other programs found on a Windows machine for comparision can be found at the bottom of this page.
Performance Charts for Anti-Virus Programs
How well does anti –virus protection protect, disinfect, and quarantine Trojans from your computer
How Well Does Anti-Virus Protect
Trojan viruses often infect computers via downloaded software and programs off the internet. Anti-virus protection plays a vital role in protecting, disinfecting, and quarantining Trojan viruses from a computer. Although most Anti-Virus software is capable of handling well-known Trojan viruses, new updates are essential to ensure your system can handle newly created Trojan viruses. Even with constant virus definition updates on an Anti-Virus program, a user cannot fully depend on the Anti-Virus to take care of all their protection needs.In order for Anti-Virus to be more effective in protecting a computer system, a combination of virus definition updates, computer updates, and caution from the user is required. The user should take caution when downloading or opening sources via the internet. It is estimated that around 100-500 new viruses are released into the internet every day, and out of these, Trojans populate this new group of viruses. Virus protection is a constant game of keeping up to date on virus definitions. Commercial anti-virus software will often update itself automatically over internet once a month or more. Free or low-cost anti-virus software needs to be monitored closely as they often do not update themselves automatically.
The bottom line to this question of Anti-Virus effectiveness is simply how well the Anti-Virus used in combination with other computer protection strategies.
For Free Anti-Virus Protection (such as that provided by AVG[1]) the user has to update their software manually, but even in this case, updates for these particular types of software do not come often. A computer that has an Anti-Virus that is not up to date on virus definitions leaves the computer vulnerable to attacks from Trojan Viruses. For this reason, it is highly suggested to invest more money to ensure that your system can defend against the constant influx of Trojan viruses being released into the internet everyday.
Disinfect and Quarantine a Trojan
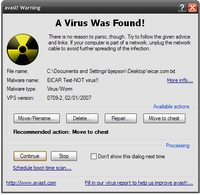
Disinfecting your computer from a Trojan Virus can be as simple as deleting temporary internet files as well as finding the file and deleting it manually. Most of the time Anti-virus protection will be able to find the Trojan, but in some cases, a Trojan will attach itself to legitimate files and documents waiting to be opened by the user. In these cases, the Trojan virus is much harder to find by both anti-virus protection and manual search. Once a Trojan Virus has been identified on your system, the best way to disinfect the virus is to run virus scans provided by anti-virus software. In most cases the anti-virus software will allow the user to remove the virus. After the scan has finished and the virus has been removed, a system restart is required. After the system restart, another scan is recommended to ensure that the Trojan has been fully removed from the system.
In order to fully protect your computer from Trojan viruses, a combination of system updates, anti-virus protection, and being aware of files being opened and downloaded are required. There are many anti-virus programs available on the market, but there is a way to distinguish the good from the bad. Anti-Virus software that is reliable and most frequently used are those who have ease of use, fast virus definition updates, fast system scanning times, and inordinate technical support. Users should be cautious when looking for online reviews on Anti-Virus software as many company's bias their information to make their software appear superior to others.
Is Anti-Virus Necessary?
The average user opens emails, allows ActiveX[2] to run, JAVA[3] to run, and even makes purchases that come with software. All of these actions can introduce viruses to their systems. It is possible to run a system without Anti-Virus software, but in order to keep your system virus free, a user could practically not do anything productive.
Actual Forum Conversations
In the following case, a user receives a Trojan horse virus, and does not know what directions to follow in order to remove it. Some users resort to online forums in order to get help with their virus problems.
"I have the Trojan horse virus PSW.Bispy. A and Bispy.B. There are others as well found in c:\windows\biprep.exe and downloader.small.4.BQ and c:\windows\CS4P081.exe. Any ideas on how to get rid of these? Any info would be great. Thanks"
In response to this forum comment, another user states:
"You should not need to reformat.firstly you should download avg'sfree antivirus.its at grisoft. next if you have windows m.e it is quite easy to get rid of the Trojan horses.run avg and it will heal ALMOST all the files.you will then be left with a file of the Trojan (or several files depending on which it is) in your restore file.make a note of the numbers that avg comes up with these will be cpy files.then you will need to unhide all hidden files. this will result in showing your restore file DO NOT DELETE THIS FILE... next right click my computer.then right click properties.click the performance tab.at the bottom of that page click the file system tab.on the next page click troubleshooting.then on the final page find the disable restore file and check the box and click apply.you will then need to restart your computer.it might start in safe mode but usually M.E starts straight up.before looking for the files by hand open my computer then open c drive and right click on the restore file you will be presented with a chance to scan again with avg do this and you will probably find the Trojan has automatically been deleted of not you will have to search for the files by hand and delete them. this sounds like a a lot of work but it only takes about 5 mins from start to finish once you have avg installed.i get Trojans as reguler as clockwork and find this is as easy a way as any to get rid of them again.for other malware i suggest "spybot search and destroy 1.2" this gets rid of spyware and also CWShredder for any other annoying little problems.all three can safely be run side by side and all are free for home users.hope this helps some of you at least."
In most cases, those who already have Anti-Virus are alerted much earlier about the Trojan virus than users that do not have an anti-virus software. In some cases this may prove to prevent damages to your system that would have otherwise been present. Also, those who believe they have a Trojan Virus on their system, and do not have Anti-Virus software normally resort to downloading or buying Anti-Virus just to get rid of their Trojan Virus.
Conclusion
For general users, anti-virus software is a good pre-cautionary program. It will find and stop harmful Trojans that you have unknowingly downloaded onto your system. However, anti-virus software can be ineffective against certain Trojans even with constant updates. Such Trojans include SubSeven and BioNet. That is why it is extremely important to know the source that you are downloading from is reliable and you do not open email attachments from unknown senders as they may have executable files containing Trojan viruses that will infect your computer if the program is run.
References (online Sources)
What is a Trojan Virus?(Kathryn Dupuis)
http://www.ircbeginner.com/opvinfo/trojan-virus.html
http://www.irchelp.org/irchelp/security/trojan.html
http://www.tech-faq.com/trojan-horse-virus.shtml
http://ezinearticles.com/?Famous-Trojans---Tony-Blair-Trojan&id=860536
http://www.richardpresents.com/Whats_%20a_%20Firewall.htm
http://www.scambusters.org/viruses.html
http://www.webopedia.com/DidYouKnow/Internet/2004/virus.asp
http://antivirus.about.com/od/whatisavirus/g/trojan.htm
http://compnetworking.about.com/cs/worldwideweb/g/bldef_trojan.htm
http://www.tml.tkk.fi/Opinnot/Tik-110.501/1997/viruses.html#2.General%20information%20of%20computer
http://service1.symantec.com/SUPPORT/nav.nsf/docid/1999041209131106
http://www.faqs.org/faqs/computer-virus/faq/
http://www.simovits.com/sve/nyhetsarkiv/1999/nyheter9902.html
http://www.2-spyware.com/trojans-removal
http://www.pandasecurity.com/homeusers/security-info/about-malware/general-concepts/concept-2.htm
What applications (sites/ emails/ downloads) infect your computer with Trojans (Santi Churphongphun)
http://www.howstuffworks.com/virus.htm
http://en.wikipedia.org/wiki/Computer_virus
http://www.learnthenet.com/english/html/37virus.htm
http://www.bbc.co.uk/science/hottopics/computerviruses/
http://technology.newscientist.com/channel/tech/electronic-threats
http://www.virus-scan-software.com/virus-scan-help/answers/the-history-of-computer-viruses.shtml
http://www.itsecurity.com/features/top-zombie-trojan-bots-092507/
http://www.news.com/File-sharing-programs-carry-Trojan-horse/2100-1023_3-801599.html?tag=txt.3
http://www.pier55.com/Internet/Security-Trojan-Horse-Virus.shtml
http://www.pcsecurityalert.com/pcsecurityalert-articles/trojan-horse-virus.htm
http://www.web-source.net/pc_security/pc_security_trojan_horse_viruses.htm
http://ezinearticles.com/?How-Trojan-Horse-Viruses-Can-Infect-Your-Computer&id=285990
http://www.emsisoft.com/en/kb/articles/tec021007/
http://www.trojan-horse.info/en/index.aspx
http://hacker-eliminator.com/trojansymptoms.html
http://www.hometechanswers.com/pc-security/trojan-horse-virus.html
What is anti – virus protection? (Mark Sauverwald)
http://anti-virus-software-review.toptenreviews.com/
http://en.wikipedia.org/wiki/Anti-virus_software
http://www.codinghorror.com/blog/archives/000803.html
http://www.thepcspy.com/read/what_really_slows_windows_down/5
http://www.pcmag.com/category2/0,1738,4796,00.asp
http://www.hicom.net/~oedipus/virus32.html
http://www.pcworld.idg.com.au/index.php/id;316975074
http://en.wikipedia.org/wiki/Real-time_protection
http://www.webopedia.com/TERM/O/on_demand_scanner.html
http://searchwindowssecurity.techtarget.com/whitepaperPage/0,293857,sid45_gci997698,00.html
http://www.cybercity-online.net/Trojan.html
http://www.codinghorror.com/blog/archives/000491.html
http://www.shareware-beach.com/2007/02/the-value-of-os-disk-images/
http://www.thepcspy.com/read/what_really_slows_windows_down/5
http://www.intranetjournal.com/articles/200210/ij_10_29_02a.html
http://www.privsoft.com/archive/psc-bionet.html
(Effectiveness) How well does anti –virus protection protect, disinfect, and quarantine Trojans from your computer. (Brad Soon)
http://www.irchelp.org/irchelp/security/trojan.html
http://support.microsoft.com/kb/129972
http://en.wikipedia.org/wiki/Trojan_horse_(computing)
http://www.ehow.com/how_2124668_remove-trojan-virus.html
http://grownupgeek.com/antivirus
http://reviews.cnet.com/Labs/4520-6603_7-5020816-10.html
http://anti-virus-software-review.toptenreviews.com/
http://www.antivirusprotection.ca/
http://www.wilderssecurity.com/showthread.php?t=50662
http://answers.google.com/answers/threadview?id=452561
http://firsttube.com/read/Is-Antivirus-Software-Really-Necessary